LOCKY RANSOMWARE
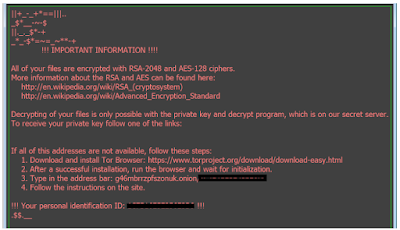
Locky ransomware is malicious program spreading through spam emails which lock your computer or network connected system by encrypting it. To decrypt your devices, it asks for ransom in bitcoins. At the initial stage, it was using fake Dropbox domains to spread ransomware. This malicious program spread zip or documents having extension .exe(although it varies) which have VB script(.vbs). It is run by the hacker through various email campaigns which included 23 million emails. Locky ransomware is frequently updated from initial days of launch.
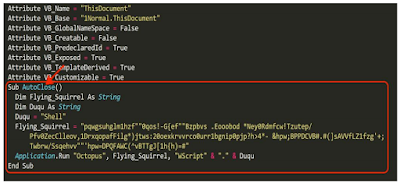
PROCESS OF ATTACK
Updated locky ransomware does not trigger by itself running the script present in word document macro. It waits for the user to close the fake document. The script run in the background to encrypt computer contents. Script run to download payload and payload is invoked from %appdata% folder. The message is displayed when commands are fully executed.
HOW TO BE SAFE FROM LOCKY RANSOMWARE
1. Do not open unknown emails from an unknown person or promotional emails.
2. Enable two step authentication on email ids.
3. Never download email attachment with .exe extension.
4. Don’t enable editing or macro in downloaded files.
5. Install security software and regularly update your system.
6. Perform regular backup of your system.
7. Disable macro in Microsoft office and Remote desktop connections.
8. Don’t install unwanted software.
9. Install firewall from being your system exploited.
10. Block attachment of malicious extension.
By -Vijay Bhushan




No comments:
Post a Comment